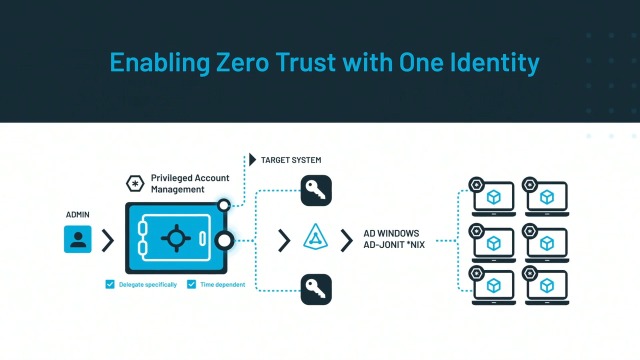
Making Zero Trust Real with One Identity. Let's start with the concept of Zero Trust. It simply means that your default stance is of no trust, and you achieve that by removing all unnecessary or excessive access rights and replace those with just-in-time delegation and accurate provisioning.
For privileged users, this means eliminating the sharing of passwords and dynamic approval workflows for administrative actions. With a Least Privileged stance, every admin user gets just enough permission to do their job-- no more, no less.
While Zero Trust is a conceptual framework, making it happen does not need some specific tools. One Identity technologies help you in automating these workflows. And with features like Approval Anywhere, we make sure that user experience is as smooth as possible.
Another One Identity feature helps extend your Zero Trust posture to your hybrid environments. Linux servers, developer workstations, executive MacBooks are all covered by proper tooling and technology.
Let's review the basic tenets of Zero Trust, then, as phrased by the National Institute of Standards and Technology. All data and all computers are considered resources. All communication must be secured no matter the network location.
Access to these resources is granted on a per-session basis. All resources need authentication and authorization before access. Access to resources is not fixed but determined by a dynamic policy, which takes into account the client identity; the application; the requesting asset; and may include behavioral, biometric, or environmental variables.
The organization monitors and measures integrity and security posture for all assets. The organization logs all information about the current state, network infrastructure, and communications.
One Identity can help you harden your security posture. Find out more about how you can secure the organization, support digital transformation, drive operational efficiencies, and enable compliance.
 02:16
02:16
