What is CTEM (continuous threat exposure management)?
The CTEM framework was originally coined and promoted by Gartner, as a modern cybersecurity program to redefine the approach to attack surface management. Gartner describes CTEM as “a program that surfaces and actively prioritizes whatever most threatens your business.”
The five-step program aims to transform our approach to cybersecurity from a reactive, episodic method to a more proactive and fundamentally safer strategy. CTEM, however, is not a technology or solution, and no vendor offers “CTEM” as a product. Instead, there are products and solutions that are suitable investments for organizations adopting the CTEM framework.
Why is CTEM important?
What makes CTEM different?
The CTEM program consists of the following five stages:
Stage 1: Scoping
The first step of the CTEM cycle is
to define the attack surface of the organization, the sum of all systems and
all entry points that could serve as a potential target of a cyber-attack. The
CTEM framework expands on the traditional definition of devices, apps and
business applications by including items like corporate social media accounts,
online code repositories and sensitive data stored in third-party systems or
the employees’ personal devices.
Stage 2: Discovery
In the second proposed step,
organizations drill deeper and identify the unique assets and the associated
risk profiles. This needs to be a rigorous process that can find hidden
assets, non-obvious entry points, risks of misconfiguration, etc. It must also
include IAM assets like identities and access rights. The result of the
discovery process is a complete matrix of assets, vulnerabilities, threats,
and an accurate assessment of business risk and potential impact.
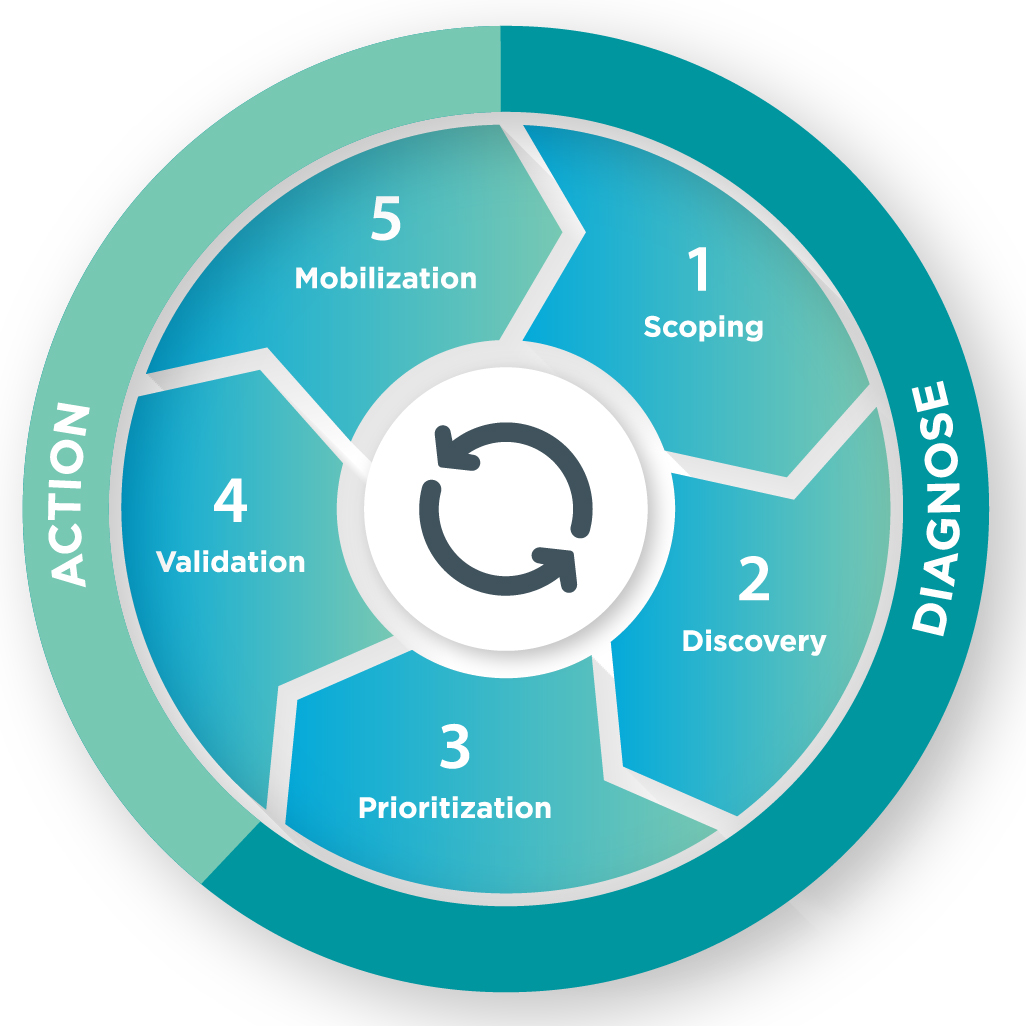
Stage 3: Prioritization
Taking this matrix further is
the process of prioritization, a ranked list of assets discovered based on
threat urgency, risk level and risk tolerance, and the effectiveness of
potential compensating access controls. This will result in an actionable list that
allows to prioritize high-risk, high-vulnerability assets first, with the
largest results to the security stance of the organization.
Stage 4: Validation
This stage involves validating the
assumptions about vulnerabilities and the threat landscape made in the
previous three stages. It confirms vulnerabilities, attack vectors and the
effectiveness of the proposed response strategy.
Stage 5: Mobilization
The final stage of a CTEM
program is getting the whole organization behind the proposed remediation
effort. The objective here is to communicate the plan to all stakeholders,
including business decision makers, and to operationalize the findings,
turning them into clear action. The framework calls out approval and
implementation processes, deployment plans for the planned mitigations and
document cross-team workflows.
Program vs project
The CTEM framework considers threat management a program, not a project. The key difference is the open-ended nature of the program, which is designed to run without a pre-defined endpoint or deliverable. In contrast, projects have a specific goal, and are performed and managed to deliver that goal in the most efficient way.
As indicated by the name, CTEM is defined as a continuous, circular scope-discover-prioritize-validate-mobilize process, without a defined end state. This iterative approach fits particularly well the ever-changing nature of the cyber threat landscape, allowing organizations to reassess the environment periodically and adapt/adjust to the changing parameters.
The CTEM framework also mandates developing processes for each stage, with repeatable outcomes for each.
What’s the difference between scoping and discovery?
How does CTEM relate to traditional vulnerability management / attack surface management?
Traditional attack surface management (ASM) is a process of identifying, monitoring and managing internal and external assets that are potential attack targets. While this sounds similar to CTEM, traditional ASM is focused on scanning the exposed assets for vulnerabilities and patching/updating the assets found vulnerable. This is characterized by its reactive nature: the existing set of assets is checked every time a new threat is found, based on one-dimensional data like CVSS scores.
With CTEM, the focus is on getting a deep understanding of the attack surface of an organization and accurately categorizing the exposed assets according to business impact. It also proposes a much larger scale of assets to protect. In addition to traditional ASM scope of servers and endpoints, CTEM includes assets like third party data storage, online code repositories and even corporate social media accounts – all highly relevant organizational assets in light of recent breaches.
Key benefits of CTEM
The single most important benefit is an immediate improvement in cyber resilience – in line with the core aim of the CTEM framework. Organizations running the program should be able to deploy better protection for non-obvious and hidden assets, and they should be able to direct the security effort more effectively towards the most exposed and most risky assets.
As a result of running a CTEM program, organizations get a better, deeper understanding of their cybersecurity posture and the impacts various breach scenarios can inflict. This means decision makers will be able to direct resources towards the most impactful cybersecurity efforts, maximizing ROI on security investment.
While CTEM asks important questions about the threat landscape, it doesn’t concern itself with specific threats – this allows organizations to move to anticipate threats and proactively mitigate risk before it materializes.
