Hi. My name's Todd Peterson. I'm a product marketing manager on the Identity and Access Management Team here at Dell Software. And today, we're going to talk about privileged account management. Let's get started. We'll turn to the Dell XPS One 27-inch touch screen.
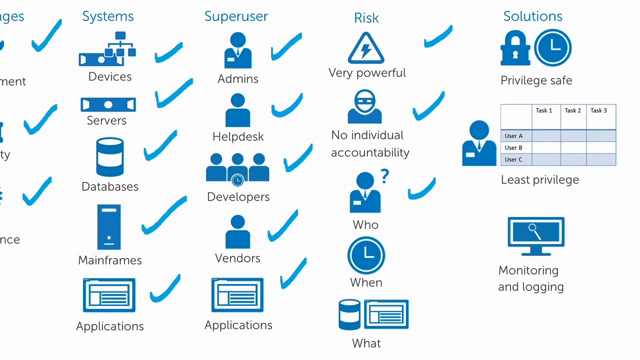
As everybody realizes, privileged account management is a major challenge, and one of the largest challenges in identity and access management. Some of the specific things that everybody faces-- and I'm sure you're the same-- is that it's very difficult to manage privileged accounts. There's a large security risk. Most breaches happen because of misuse or abuse of privileged accounts.
And they're very touchy from a compliance standpoint. Virtually every regulation requires that you control access to privileged accounts and that you enforce separation of duties with those privileged accounts. So from a management security and compliance standpoint, they're very difficult and very challenging.
One of the reasons they're so challenging is you have so many systems. You have devices with privileged accounts. You have servers with privileged accounts, databases, mainframe applications. Everything that runs your IT organization has a privileged account. And those privileged accounts have risk associated with them.
The superusers that need to use those accounts range from administrators, help desk people, developers, even third-party vendors and other applications that need to talk to databases or other applications to exchange information. They need a privileged account in order to do that as well. So there's a lot of risk associated with the privileged accounts. They are very powerful.
They allow you to do anything and everything that you may need to do on a system, even things that you maybe should not do on the system. There's no individual accountability. Because the account is tied to the system and not to an individual person, there's no way of knowing who did what, when they did it, or even natively what they did with the account.
So there's a number of solutions to help solve the privileged account management problem. And ideally, you would use all three solutions for a complete, holistic approach. The first is a privilege safe, which we'll talk about in a second, followed by implementing a least privileged access model, and then the ability to monitor and log what people do with those super user accounts when they're issued them. Let's move on.
So first is privilege safe technology. Imagine what you would do if you were manually controlling all of your privileged accounts. You'd have the passwords written in a binder, locked in the safe. And when anybody ever needs to do work, you're going to go get it out of the safe, give it to them, watch what they do, come back when they're done, and go in manually and change the password.
Well, a privilege safe-- like the one from the Dell One Identity Solutions-- allows you to automate and secure that whole process. So here's how it works. I'm an administrator, and I need to access a system to do some work. I'm going to make a request through the privilege safe. That request is going to be checked against the policy. And it's either going to ask my boss for approval or grant me access because I've been preapproved.
Once authorization is given, the privilege safe issues me the password. I'm then able to do the work that I needed it to do. But you can also use the privilege safe to audit what I'm doing, to watch what I do. You can control what I'm able to do. Some commands I may be able to perform, others I may not. And you can limit the time. I only have it for half an hour, and I'm only able to reset a password or whatever. And you're watching it the whole time.
Then when I'm done, you turn it back in, and the safe automatically changes the password, locks it back away for the next person to use. So it's a very secure, very automated way to overcome the problem of shared passwords and lack of individual accountability with those shared passwords.
The second thing that you'll want to do is to implement a least privilege model, because you don't always want to give everybody the full administrative credential-- for instance, the root account on Unix systems, or the admin account on any applications or Active Directory. You'll want to give people the ability to do their jobs, but not the ability to do more than their jobs. And so you will delegate that access.
One of the great examples of how to delegate access is an open source tool that comes with every Unix and Linux box called sudo, S-U-D-O. It stands for "super user do." And it allows you to write a policy file that says, user A can do a specific thing and not another thing.
The problem with sudo is it's applied on every single server. So in our example here, we have four Unix servers. Each of those servers has sudo on it. And each of those copies of sudo has a file that's been written that says what each user is able to do and not do. Problem is, if you have 100 or 1,000 or more servers, you have a lot of redundancy, a lot of places that things can go wrong, and a lot of policy files to keep track of.
The Dell One Identity Solutions has a way to overcome the native shortcomings of sudo. Rather than write a policy file individually on every single server, you're going to centralize them all in a single place, which then allows you to write the file once and push it out everywhere, which gives you consistency of policy and the ability to know that policy is accurate. In addition, that then gives you the ability to report on the policy. And it adds things like keystroke logging to the capability, so you have auditing as well.
Now another
 07:09
07:09
